Deploy AI agents to your entire organization via IdP
This guide shows you how to deploy AI agents to hundreds or thousands of users without creating individual CustomGPT.ai accounts—by leveraging your existing Identity Provider (IdP) to control access.
If your organization already uses an Identity Provider like Microsoft Entra ID, Okta, Google Workspace, or PingOne, you can grant employees, students, or partners instant access to specific agents based on attributes you define in your IdP. No invitations. No user management. No limits on end-users.
When to use this feature
| Situation | Benefit |
|---|---|
| Large organizations with 100+ end-users | Eliminate manual user invitations—access is controlled entirely by your IdP |
| Multiple departments needing different agents | HR gets the HR agent, IT gets the IT agent—all from the same URL |
| Universities and schools | Professors can restrict course assistants to enrolled students only |
| Organizations that don't want to manage users in CustomGPT | Your IdP is the single source of truth for access control |
| Partners or external users in your IdP | Grant controlled access without creating CustomGPT accounts |
How it works
- You configure an attribute in your IdP (e.g.,
customgpt_role) and assign values to users - You create matching roles in CustomGPT.ai with Chat-Only permissions
- You share one portal URL with all users
- Users authenticate via your IdP—CustomGPT reads the attribute and grants access to the corresponding agents
- Sessions last 24 hours—users re-authenticate after expiration
Key benefit: Users are NOT created in CustomGPT.ai. They remain anonymous and can only chat. No accounts to manage, no user limits to worry about.
Prerequisites
Before you begin, ensure you have:
- CustomGPT.ai Teams plan with the IdP End-User Access feature enabled (contact sales to activate)
- SSO already configured for your organization. See SSO setup
- A custom attribute configured in your IdP that will map to CustomGPT roles
- Access to the SSO tab in CustomGPT.ai (see note below)
Who can access SSO settings?
The SSO tab is only visible if the feature is enabled on your plan, and only to the account owner or users with non-organization accounts (i.e., accounts that existed before being added to the organization). Users auto-created via SCIM or SSO cannot access SSO settings. This is a security measure introduced before the roles and permissions system. If you need to delegate SSO management, contact support.
Step 1: Set your agents to Private visibility
Before configuring IdP access, ensure the agents you want to protect are set to Private visibility.
- Go to your agent's Personalize setting
- On the Personalize page, click on the Security tab
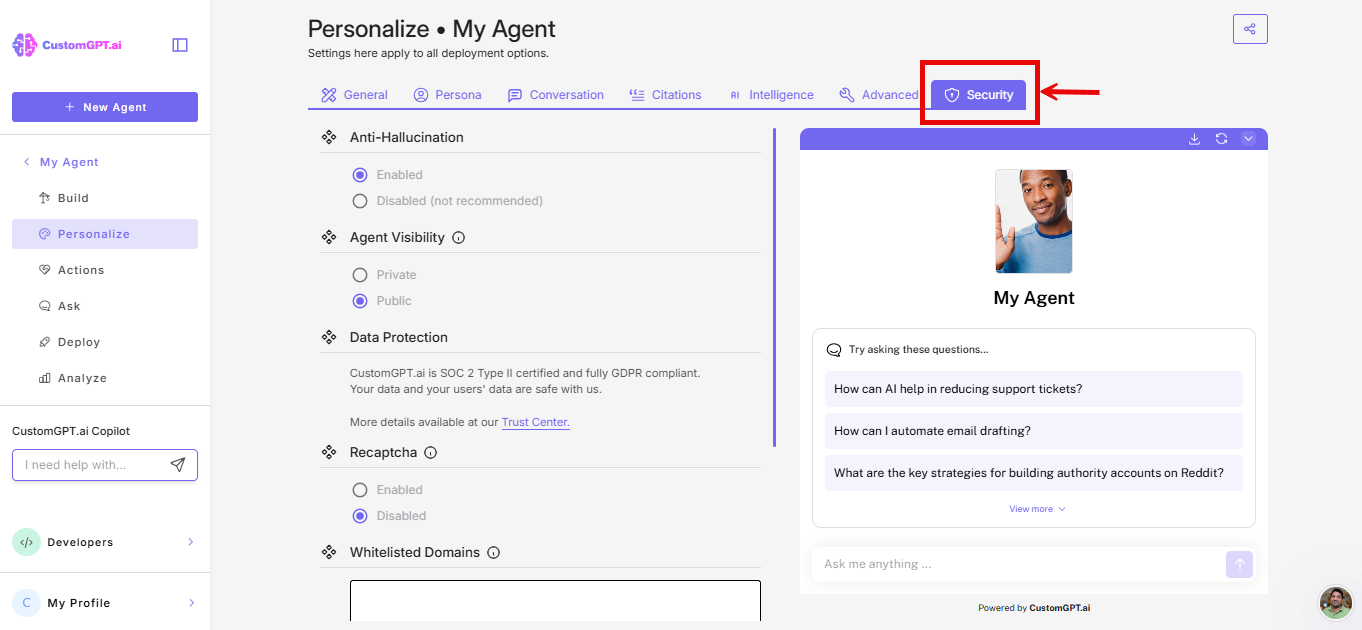
- Scroll to Agent Visibility, select Private
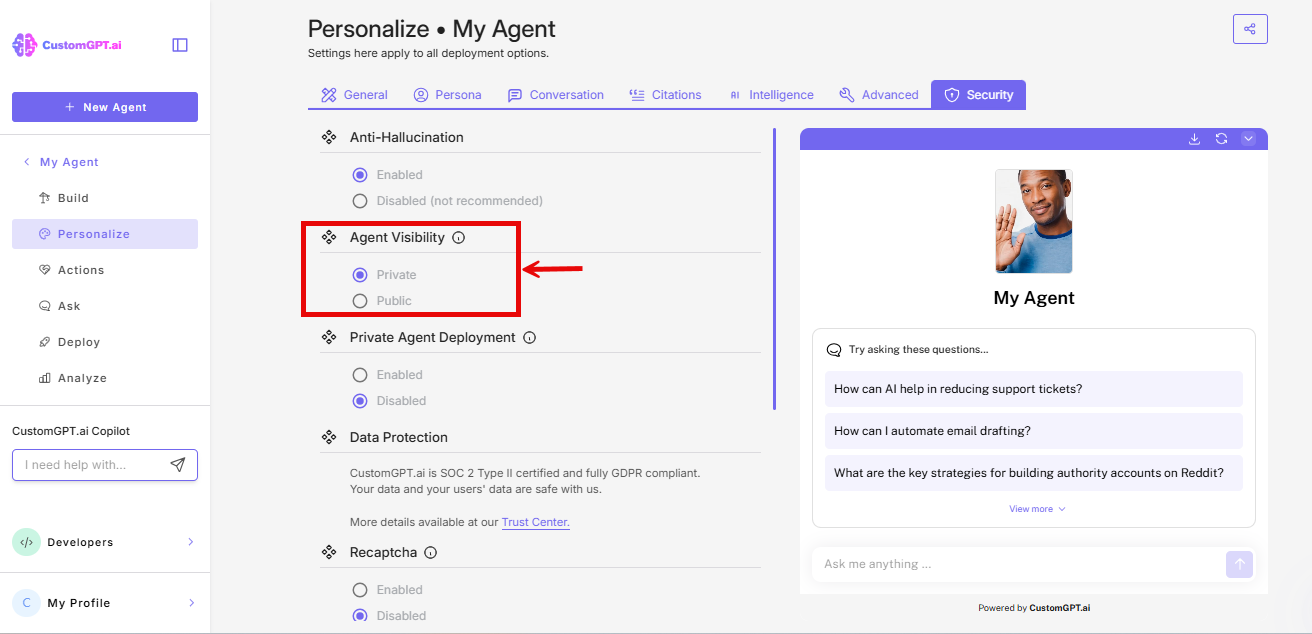
- Click Save
ImportantAgents must be set to Private for IdP-based access control to work properly. Public agents can be accessed by anyone without authentication.
Step 2: Configure an attribute in your IdP
Work with your IT team to configure a custom SAML attribute in your Identity Provider. This attribute will tell CustomGPT which role(s) to assign to each user.
What CustomGPT needs:
| Requirement | Details |
|---|---|
| Attribute name | You choose (e.g., customgpt_role)—you'll enter this in CustomGPT later |
| Attribute value | Must exactly match a role name you create in CustomGPT |
| Case sensitivity | Case-sensitive—Sales-Team ≠ sales-team |
| Maximum length | 255 characters |
| Reserved names | Cannot use: Owner, Administrator, Team Administrator, Chat-only, Member, Super Admin |
NoteThe specific steps to create and assign custom attributes vary by IdP. Consult your IdP's documentation or your IT team for implementation details.
Step 3: Create matching roles in CustomGPT
Create a role in CustomGPT.ai that exactly matches each attribute value you configured in your IdP.
- Go to Teams → Roles
- Click Create Custom Role
- Configure the role:
- In the Agents section, select which agents this role can access
- Click Submit
Critical: The role name must be an exact, case-sensitive match to the attribute value from your IdP. If your IdP sends
partner-support, your role must be named exactlypartner-support.
Step 4: Enable IdP End-User Access in CustomGPT
- Click My profile icon in the bottom-left corner
- Click My Profile from the dropdown
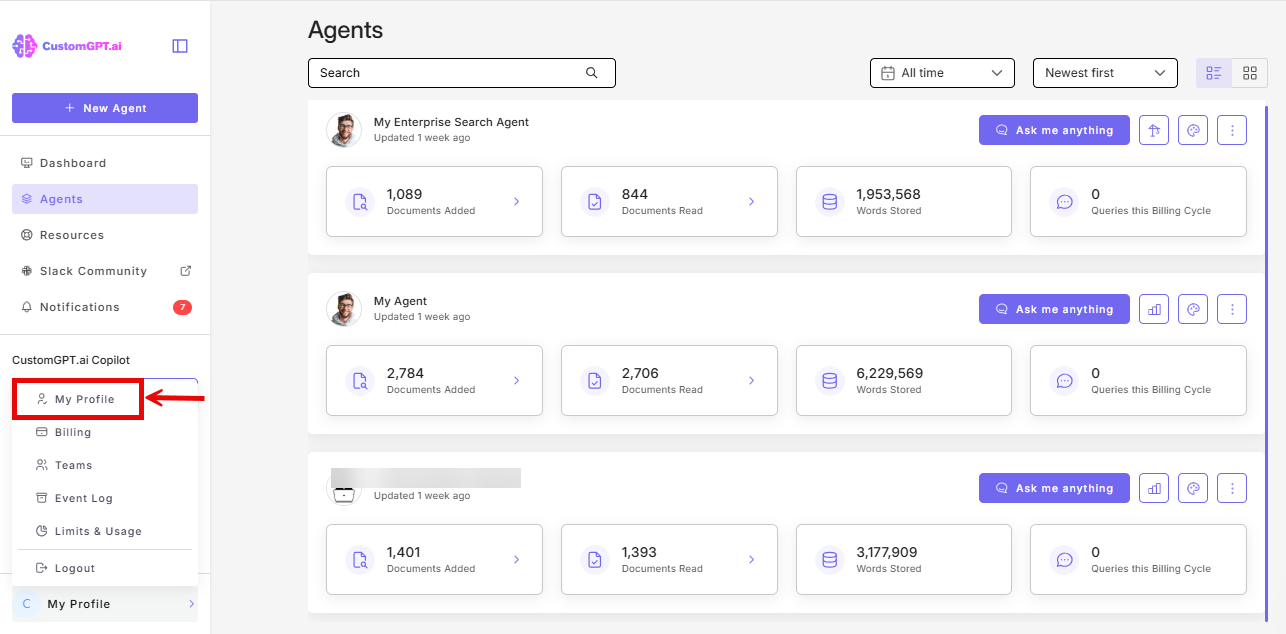
- Click the Single Sign On (SSO) tab
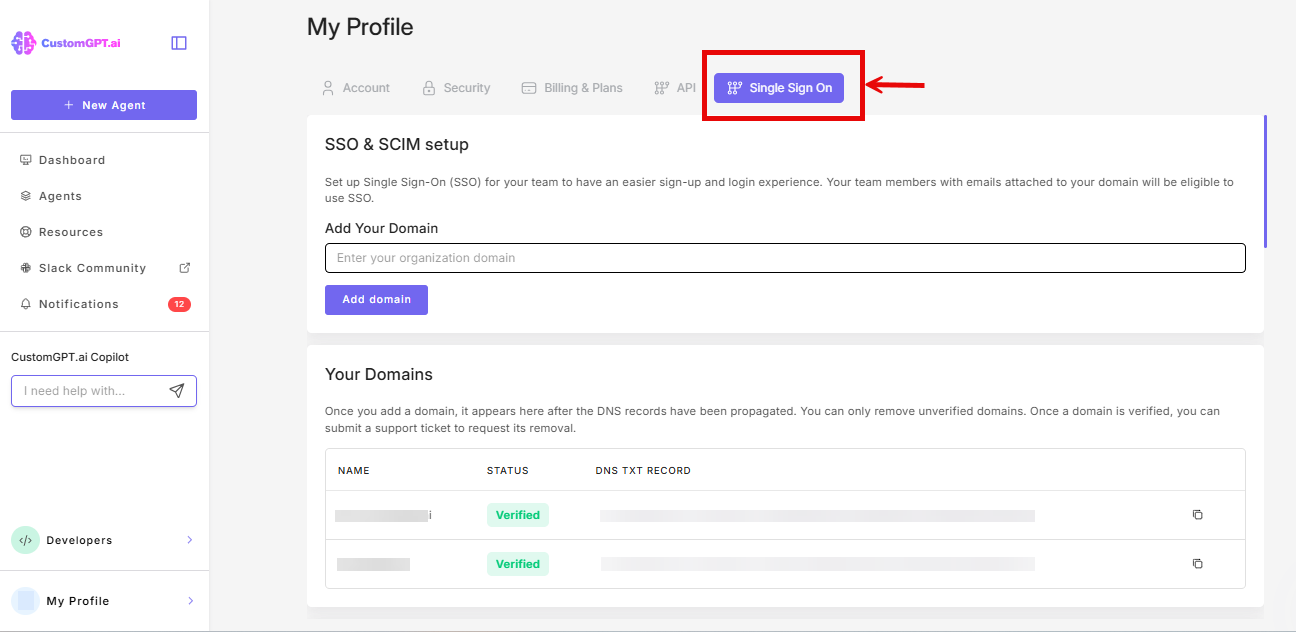
- Scroll to the IdP End-User Access Control section, and toggle On Enable End-User IdP Access
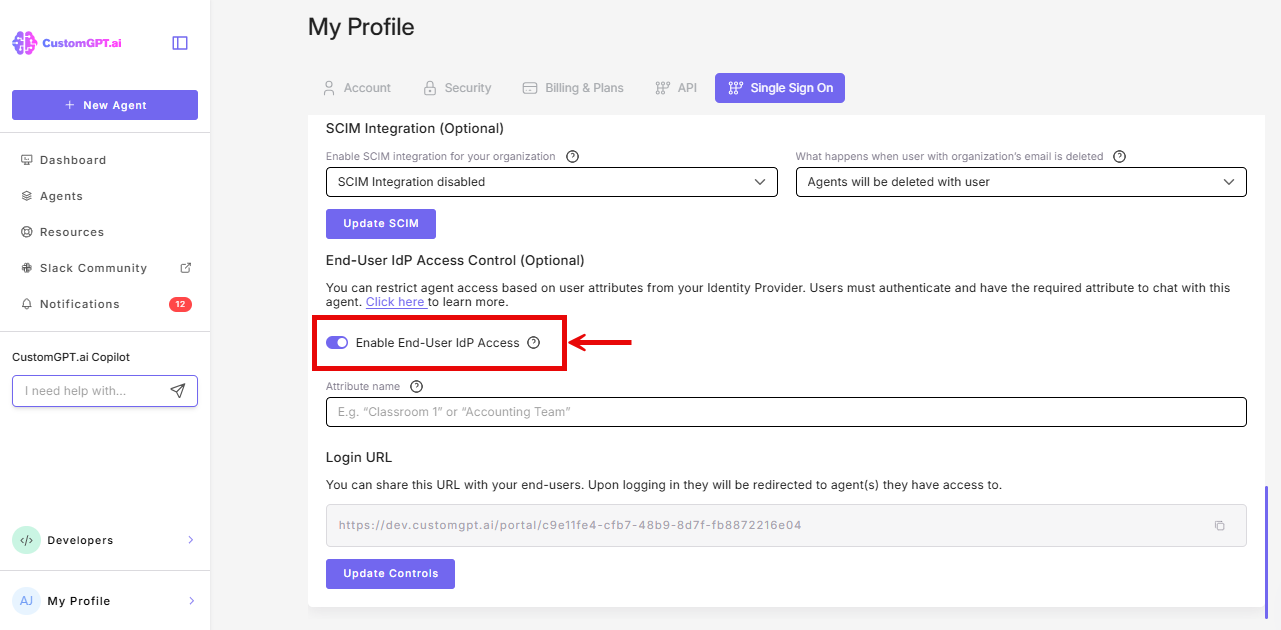
- Enter the attribute name you configured in your IdP (e.g.,
customgpt_role)
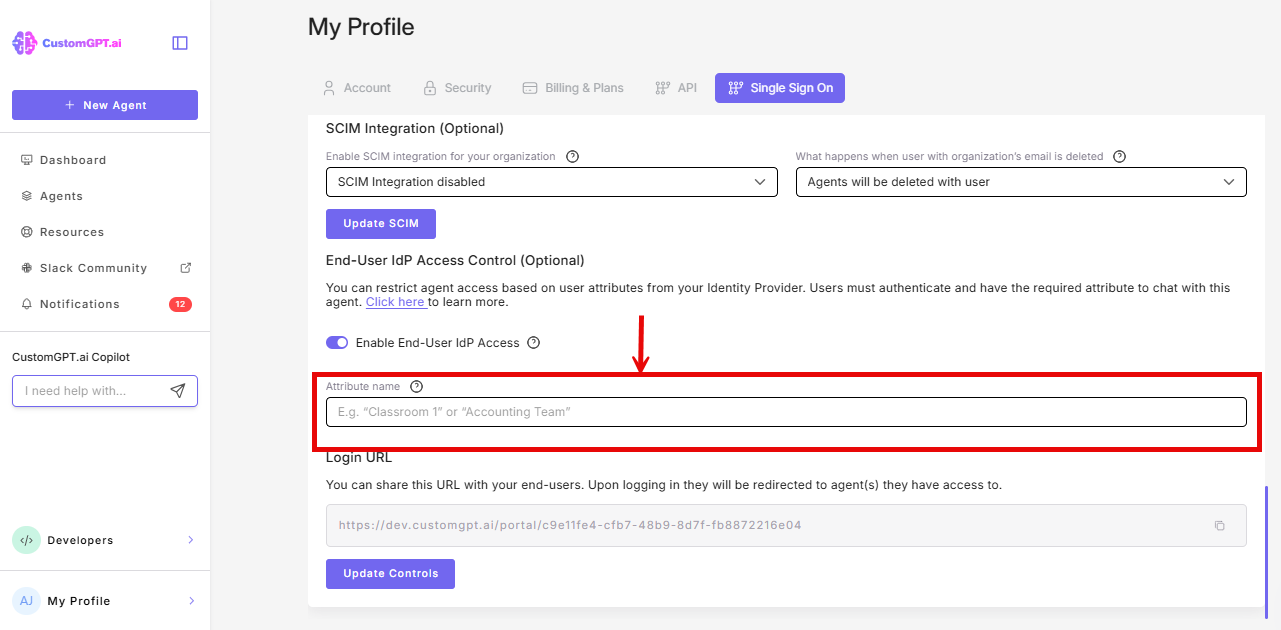
- Click Update Controls
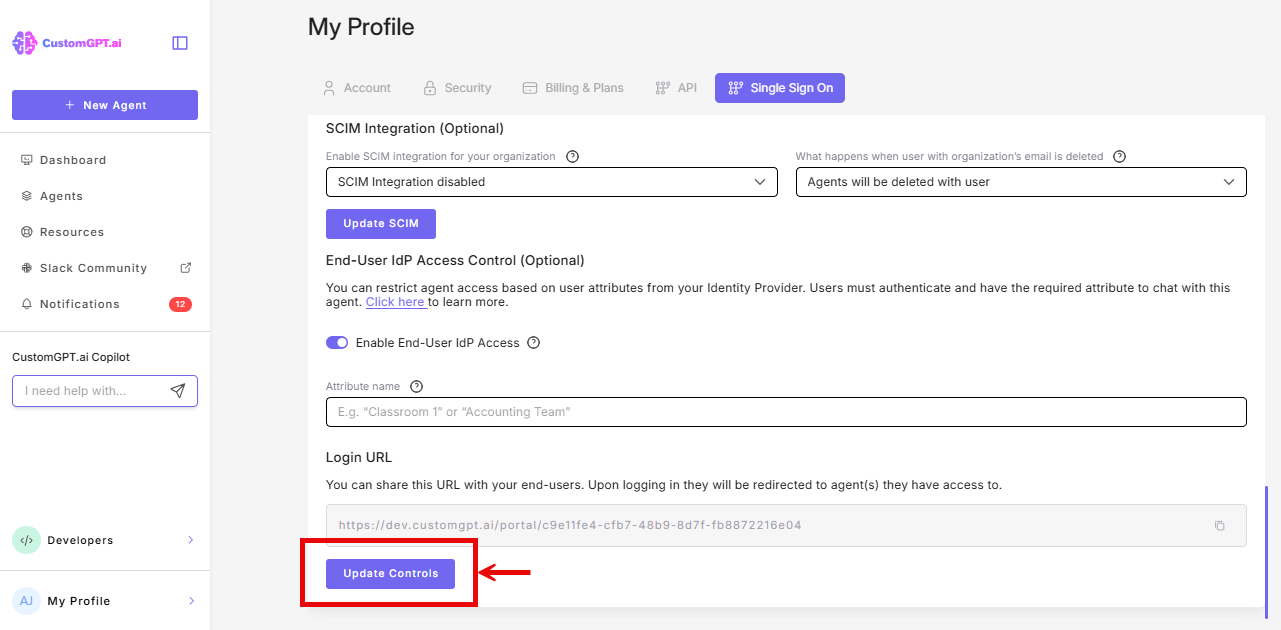
- Copy the generated Portal Login URL
Portal URL format The URL is unique to your organization and looks like:
https://app.customgpt.ai/portal/[random-string]
Step 5: Test the configuration
- Open an incognito/private browser window
- Navigate to your Portal Login URL
- You should be redirected to your IdP for authentication
- Log in with a test account that has the correct attribute value
- After authentication:
- If the role has access to one agent: you're redirected directly to chat
- If the role has access to multiple agents: you see a portal listing all accessible agents
What end-users experience
Authentication flow
- User visits the Portal Login URL
- User is redirected to your organization's IdP
- User authenticates with their existing credentials
- User is redirected back to CustomGPT with a 24-hour session
Agent access
- Single agent: User goes directly to the chat interface
- Multiple agents: User sees a selection portal and chooses an agent
- Switching agents: User can revisit the Portal URL to select a different agent (within the 24-hour session)
- No "back to portal" button: Once in a chat, users must use the Portal URL again to switch
Session behavior
| Aspect | Behavior |
|---|---|
| Session duration | 24 hours (fixed, not configurable) |
| Session expiry | User must re-authenticate via IdP |
| Conversation continuity | Each authentication starts a new conversation |
| Conversation history | Not preserved between sessions |
Branding
The only CustomGPT.ai branding visible is the "Powered by CustomGPT" badge, unless removed via white-labeling.
Use case examples
Enterprise: Department-based access
Scenario: A company wants HR, IT, and Sales departments to each have their own AI assistant.
Setup:
- In your IdP, create an attribute
customgpt_rolewith values based on department - In CustomGPT, create three roles:
hr-team,it-team,sales-team - Assign the HR Knowledge Agent to
hr-team, IT Support Agent toit-team, etc. - Share the same Portal URL with all employees
Result: Each employee authenticates once and sees only the agent(s) relevant to their department.
Multi-department users: If an employee belongs to multiple departments, configure your IdP to send multiple attribute values. They'll see a portal with all their accessible agents.
Education: Course-specific agents
Scenario: A professor has three courses (MATH101, MATH201, PHYS101) each with a course assistant agent.
Setup:
- Configure your university IdP to send course enrolment as an attribute
- Create roles in CustomGPT matching course codes:
MATH101,MATH201,PHYS101 - Assign each course agent to its corresponding role
- Share the Portal URL with students
Result: Students only see agents for courses they're enrolled in.
When a student drops a course: The IdP attribute changes on the university's side. The student's current session (if active) continues until it expires (up to 24 hours). On next authentication, they'll only see agents for their current courses.
Partners and external users
Scenario: Grant vendor partners access to a support agent without creating CustomGPT accounts.
Requirements: Partners must exist in your IdP system (or a federated IdP).
Setup:
- Add partners to your IdP with an attribute like
customgpt_role: partner-support - Create a
partner-supportrole in CustomGPT - Assign the Partner Support Agent to this role
- Share the Portal URL with partners
Choosing the right access method
| If you need... | Use this approach |
|---|---|
| Access for 100+ users with minimal management | IdP End-User Access (this feature) |
| Individual user tracking and conversation history | Private Agent Deployment with CustomGPT accounts |
| Quick setup without IdP | Public agent with reCAPTCHA |
| Full user management and permissions | CustomGPT Teams with invited users |
IdP access vs. traditional accounts
| IdP End-User Access | Traditional user accounts |
|---|---|
| No user limit | Users count against plan limits |
| No invitations needed | Must invite each user |
| IdP is single source of truth | Manage access in two places |
| Anonymous analytics | Per-user tracking |
| No conversation history | Persistent conversation history |
| Requires existing IdP | Works without IdP |
Current limitations
- Deployment: Currently works only with the Portal URL (Share Link) and Embedded deployments.
- Custom domains: Portal URL cannot be customized or white-labelled at this time
- Analytics: Cannot track usage by role or see which attribute was used
- Audit logs: Detailed access audit logs not available yet
- Session duration: Fixed at 24 hours, not configurable
- Access revocation: Changes take effect on next authentication (up to 24 hours)
Troubleshooting
Users receive 403 Forbidden errors
This error appears when access cannot be granted. Check that:
- Your IdP is sending the correct attribute name
- The attribute value exactly matches a role name in CustomGPT (case-sensitive, no extra whitespace)
- The role has at least one agent assigned
- The assigned agents are set to Private visibility
Access changes aren't taking effect
Attribute changes in your IdP take effect on the user's next authentication. Active sessions continue until they expire (up to 24 hours).
Users can't continue previous conversations
Each authentication via the portal starts a new conversation. Conversation history is not preserved between sessions for IdP end-users.
For persistent issues, contact support.
Related guides
Updated 6 days ago
